

You wouldn't be cracking any strong passwords. That's in no way a dig at you or your hardware, merely a statement of confidence in the current encryption standards. If you do know of a way to crack strong passwords, then you've found a vuln in the algorithm and you should report it to the relevant authorities. Seriously.
And if you can crack certs and assymmetric crypto in general, then the RSA stock price will plummet and Fmjc001.com will likely take their place
Well I managed to crack a 36 character passphrase, upper case, lowercase, numbers and symbols in a few days. I dont know if thats good to you but I was rather happy with myself lol.
Hmm,
can you crack a WPA-PSK encrypted key like this with a temporal that resets every 10 minutes?
0z417swWM1'@((H#3$J]{,GOBW248+_@#fsdVXPq34012
This is a "crackable" encryption, and I bet even with aircrack you cant break my network. The point is, With a good key/password I think you'd be SOL. it is only simple keys/easily broken with dictionary/brute force attacks that these methods will work- especially considering the hash is disabled by default in Vista, and Linux without the User password will be useless.
My Computer
System One
-
- CPU
- T7600G Core2Duo 2.66 Ghz
- Motherboard
- Intel 945PM + ICH7 Chipset
- Memory
- 4GB DDR2 PC2-5300 667MHz
- Graphics Card(s)
- Mobility Radeon x1900 256MB
- Sound Card
- Realtek HD
- Monitor(s) Displays
- WUXGA 17"
- Screen Resolution
- 1920X1200
- Hard Drives
- 640GB 7200RPM SATA/RAID 0 (2x320GB)
and 320GB 7200RPM External
- Mouse
- Wireless Microsoft 3000
- Internet Speed
- 10 mbps/2 mbps
- Other Info
- Optical Drive:
Panasonic UJ-220 DL BD-RE (Blu-Ray)


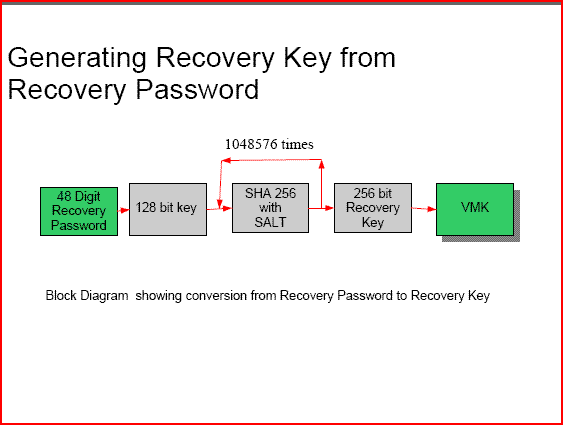
 .
.